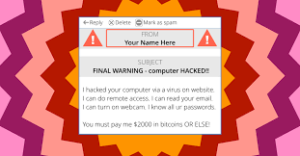
What is a Spoofed/Hacked Email Scam?
A scammer impersonate a victim’s supplier using a similar email address. The victim will be told to transfer money to a different bank account because the supplier’s regular account has been suspended or is under audit.
In another variant, scammers will hack into their victim’s email account, that of the supplier’s or business partner’s. They will monitor the email correspondence between the two and at an opportune time, send an email to their victim to request for payment to be paid to another bank account. The spoofed email used by the scammer can closely mimic that of the original email address.
These are some examples of spoofed email addresses:
| Genuine Email | Spoofed Email |
| [email protected] | [email protected] (1 replaced with a I) |
| [email protected] | [email protected] (i missing) |
| [email protected] | [email protected] (. replaced by -) |
In some cases, scammers may even use the same business logo, links to the company’s website, or messaging format to trick their victims into believing that they have received a genuine request for payment.
Victims will only come to realise that they have been scammed (often days later) when their actual suppliers call to inform them they have not received their payment.
- WHAT YOU SHOULD LOOK OUT FOR…
- WHAT YOU SHOULD DO…
- Any sudden changes to your suppliers’ or creditors’ payment instructions and accounts. When in doubt, check directly with your suppliers
- Do not make changes to your payment arrangements without verifying the email with your suppliers
- Call previously known phone numbers instead of the number reflected on the email with the new payment instructions
- Always use secured networks to reduce the risk of hacking
- Install anti-virus software and update it regularly to protect your computer system. You may consider installing free Domain Name System (DNS) protection services such as Quad9 (quad9.net) to protect against such attacks.
- Always update your Operating System (OS) when new patches are made available.
- Educate your employees about this scam, especially those responsible for making fund transfers
- Improve the security of your company’s IT infrastructure. For SMEs that wish to explore ways on how they can improve their IT security, visit SME Digital Hub
- Consider installing email authentication tools such as Domain-based
Message Authentication, Reporting and Conformance, DMARC
(dmarc.globalcyberalliance.org), which can help detect fraudulent emails.
More Cybersecurity Tips:- Global Security Alliance (GCA) toolkit: https://gcatoolkit.org/smallbusiness/
- CSA Website on cyber hygiene: https://www.csa.gov.sg/gosafeonline


